It’s quite simple to work with and setup. The only real extra step is crank out a completely new keypair that can be utilised with the hardware product. For that, there are two critical sorts that may be utilised: ecdsa-sk and ed25519-sk. The previous has broader components support, though the latter might need a Newer system.Because the backdoor
SSH support SSL for Dummies
SSH 7 Days is the gold typical for secure remote logins and file transfers, offering a strong layer of security to details website traffic around untrusted networks.without having compromising stability. With the best configuration, SSH tunneling can be utilized for a variety ofWe are able to boost the security of information on your own Laptop or
5 Simple Techniques For ssh sgdo
In addition, if an incorrect configuration directive is equipped, the sshd server may perhaps refuse to start out, so be extra watchful when editing this file on the distant server.SSH tunneling is usually a means of transporting arbitrary networking information in excess of an encrypted SSH relationship. It can be employed to add encryption to leg
Article Under Review
Article Under Review
Article Under Review
Article Under Review
 Danny Tamberelli Then & Now!
Danny Tamberelli Then & Now!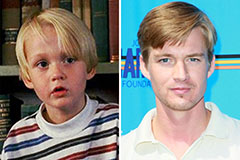 Mason Gamble Then & Now!
Mason Gamble Then & Now! Shannon Elizabeth Then & Now!
Shannon Elizabeth Then & Now! Pierce Brosnan Then & Now!
Pierce Brosnan Then & Now! Ryan Phillippe Then & Now!
Ryan Phillippe Then & Now!